
Attack Modeling a Forgotten Password System
This Attack Model maps potential attack vectors in a typical forgotten password …

MFA has one weakness that puts every user at risk.
The core of authentication relies on checking three possible traits of a person:
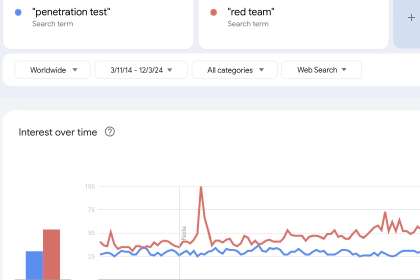
Pentesting now seems like a dirty word.
This struck me when I was reading Open AI’s recent post “Advancing red teaming …

I’m glad to see the first stand-alone cyber security legislation passing in to law today in Australia. The regulations …
The opening scene from Terminator 2 takes place on July 11, 2029. It’s eerily close to when I expect several …

There is one area of information security that is conspicuously absent from ATT&CK.
If your tooling only applies the …

At it’s core, an Attack Library is a list of all possible attacks against a component of your design. We use it almost …

Everyone? I’m not so sure…
Imagine the early 2000s… Britney Spears is playing on the radio, the …